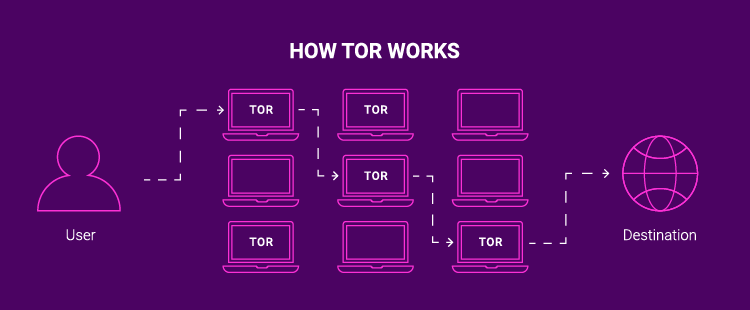
As internet privacy becomes an increasingly pressing concern, the Tor Browser emerges as a vital tool for safeguarding personal information and online activities. Central to its functionality is the torrc file, which offers a myriad of configuration options for users to explore and customize. This article endeavors to dissect the torrc file, offering insights into each configuration option and its implications. Through this exploration, users will gain a deeper understanding of how to fine-tune their Tor Browser for optimal performance and security.

Understanding the Torrc File:
The torrc file serves as the backbone of Tor Browser customization, housing a plethora of configuration options that govern its behavior. From network settings to security parameters, each option plays a crucial role in shaping the browsing experience. By delving into the torrc file, users can unlock the full potential of the Tor Browser and tailor it to their specific requirements.
Exploring Configuration Options:
- ExitNodes and StrictNodes:
- ExitNodes allows users to specify which nodes they want to use as exit points for their Tor connections, while StrictNodes ensures that only the specified nodes are used. These options provide users with granular control over their exit node selection, enhancing security and privacy.
- MaxCircuitDirtiness:
- This option determines the maximum lifespan of circuits used by Tor for routing connections. By adjusting this parameter, users can strike a balance between security and performance, mitigating the risk of prolonged circuit exposure to potential attacks.
- Bridge Configuration:
- Bridges act as alternative entry points to the Tor network, offering users a means to circumvent censorship and surveillance. The torrc file allows users to configure bridges manually, providing an additional layer of anonymity and resilience.
- Bandwidth Rate and Bandwidth Burst:
- These options allow users to limit the bandwidth usage of their Tor connection, helping to manage network resources and prevent congestion. By adjusting these parameters, users can optimize their browsing experience and minimize latency.
Conclusion:
The torrc file configuration options represent a powerful toolset for fine-tuning the Tor Browser to meet the diverse needs of its users. By delving into the intricacies of each option and experimenting with different configurations, users can enhance their online privacy, security, and performance. As the digital landscape continues to evolve, the torrc file stands as a beacon of customization and control in the quest for a safer and more secure internet.