Are you interested in exploring the mysterious world of the dark web? Look no further! In this article, we will be diving into a selection of links to onion resources dedicated to TOR sites. But first, let’s familiarize ourselves with a few key terms.
What is TOR?
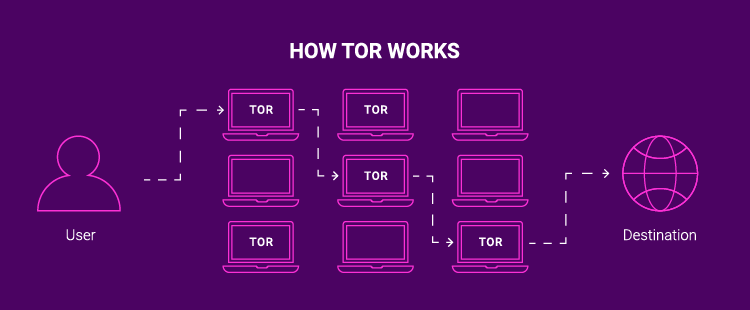
TOR, short for The Onion Router, is a browsing tool that allows users to access the dark web anonymously. By routing internet traffic through a series of encrypted nodes, TOR ensures that your online activities remain private and secure.
Navigating the Dark Web
Navigating the dark web can be a daunting task, but fear not! The following list of onion resources will guide you through this hidden realm with ease:
- Dark Web Link Directories: Websites like “The Hidden Wiki” serve as directories of TOR sites, making it easy to find a variety of resources, from marketplaces to forums.
- Reddit Communities: Subreddits dedicated to the dark web, such as r/onions, provide a platform for users to share and discover new onion links.
- TOR Search Engines: Just like Google, TOR has its own search engines like Ahmia and Torch, which allow users to search for specific content on the dark web.
Top Onion Resources
Now that we’ve covered the basics, let’s delve into some top onion resources that you can explore:
- The Hidden Wiki: This well-known directory contains a vast collection of onion links, ranging from marketplaces to messaging services.
- DuckDuckGo: Known for its privacy-focused search engine, DuckDuckGo also offers a dark web version that allows users to search for content anonymously.
- Deep Web Radio: If you’re a music enthusiast, Deep Web Radio provides a selection of streaming radio stations that can only be accessed through TOR.
Staying Safe on the Dark Web
While the dark web offers a glimpse into a world of anonymity, it’s crucial to prioritize safety and security. Here are a few tips to keep in mind:
- Use a VPN: To enhance your online privacy, consider using a reputable VPN service alongside TOR.
- Avoid Suspicious Links: Be cautious when clicking on unknown links, as they may lead to harmful or illegal content.
- Keep Your Identity Hidden: Remember to use a pseudonym and avoid sharing personal information while browsing the dark web.
Conclusion
Exploring the dark web can be both thrilling and enlightening, but it’s essential to approach it with caution. By utilizing the onion resources mentioned in this article and practicing safe browsing habits, you can navigate the TOR network with confidence. So, what are you waiting for? Dive into the depths of the dark web and uncover its hidden treasures!
References:




